This lesson is the dedicated Google login upgrade that was intentionally moved out of 018a so the login-shell lesson stays simple.
Goal
Upgrade the existing LoginActivity flow from Email/Password-only (or login shell) to support:
- Google account picker
- Firebase Authentication with Google credential
- Correct SHA1 setup so emulator/device login works reliably
Prerequisites
018a.LoginActivityFromGui.mdcompleted (login UI shell exists)018b.FirebaseProjectRtdbAuthSetup.mdcompleted (Firebase project + Auth + RTDB setup)018ccompleted or equivalent Email/Password auth wiring in place
Reference implementation (local)
- Presence commit:
11c8948681e84158c24528eda64c2125804e1499 - Commit message note (important): generate debug SHA1 and add fingerprint
What gets added in this lesson
- Google Sign-In dependency (
play-services-auth) - Google sign-in client initialization using
default_web_client_id - Google account picker launch and result handling
GoogleAuthProvider.getCredential(...)- Firebase
signInWithCredential(...)
SHA1 clarification (important)
Question:
can login from Android Emulator without dealing with SHA1 shit.
Answer:
If your students are using Email/Password or Anonymous authentication, they don’t need the SHA1 at all. It will just work.
However, if you are using Google Sign-In, Firebase needs that SHA1 to verify that the request is coming from a “trusted” version of your app. Without it, the emulator will usually throw a generic Developer_Error (Status Code 10) and refuse to show the account picker.
Teaching implication:
- Do not block
018b/018con SHA1. - Introduce SHA1 only when Google Sign-In is added.
Critical SHA1 step
Generate SHA1 from the machine debug keystore:
"C:\Program Files\Android\Android Studio\jbr\bin\keytool.exe" -list -v -keystore "%USERPROFILE%\.android\debug.keystore" -alias androiddebugkey -storepass android -keypass android
keytool is not a built-in Windows 11 command.
- It comes with a Java JDK installation.
- It is also bundled with Android Studio (which is why the command above uses the Android Studio
jbrpath directly). - If Android Studio is installed, students usually do not need any extra download for this step.
If the command above fails because Android Studio is missing or installed in a different folder:
- Check whether
keytoolis already on PATH withwhere keytool. - If not, install one of these and retry:
- Android Studio (includes bundled Java runtime/tools): https://developer.android.com/studio/install
- OpenJDK (Temurin): https://adoptium.net/temurin/releases/
Where to add this SHA1 in Firebase
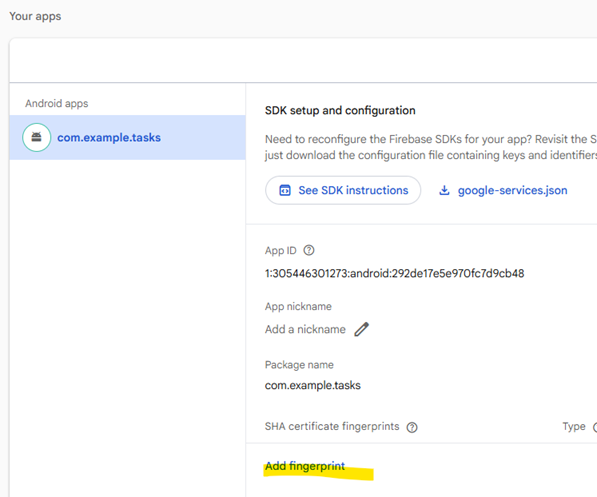
- Firebase Console -> Project settings -> General -> Your apps -> Android app ->
SHA certificate fingerprints-> Add fingerprint
Clarification:
- Yes, this is configured inside the Firebase project settings.
- It is tied to the specific Android app identity (
package + SHA) under that project.
In a shared classroom Firebase project, each student machine usually has a different debug SHA1.
Choose one classroom strategy:
- Register each student’s debug SHA1 in the same Firebase Android app
- Standardize a shared debug keystore for the class
- Teach Email/Password first and delay Google Sign-In until later
Classroom flow: one shared debug keystore (recommended for Google Sign-In lesson)
This is the lowest-friction classroom setup when many students need Google Sign-In against the same Firebase project.
Important clarification:
- You do not add the keystore file to RTDB.
- You add the keystore fingerprint (
SHA1, preferably alsoSHA-256) to the Firebase project settings for the Android app. - Students copy the shared debug keystore file onto their machine so they all sign debug builds with the same certificate.
Teacher flow (one-time setup)
- Generate a class debug keystore on the teacher machine (or choose an existing one).
- Extract the SHA1 (and optionally SHA-256) from that keystore.
- Add the fingerprint(s) in Firebase Console -> Project settings -> Android app.
- Share the keystore file with students through an internal classroom channel (USB / LMS / shared drive).
- Keep this keystore for the whole course phase so the fingerprint stays stable.
This shared keystore is for debug/classroom use only. Do not use it for release signing.
Teacher command: generate a class debug keystore (run once)
"C:\Program Files\Android\Android Studio\jbr\bin\keytool.exe" -genkeypair -v -keystore "C:\Classroom\class-debug.keystore" -storepass android -alias androiddebugkey -keypass android -keyalg RSA -keysize 2048 -validity 10000 -dname "CN=Android Debug,O=Android,C=US"
Then print fingerprints:
"C:\Program Files\Android\Android Studio\jbr\bin\keytool.exe" -list -v -keystore "C:\Classroom\class-debug.keystore" -alias androiddebugkey -storepass android -keypass android
Add the displayed SHA1 (and preferably SHA-256) to Firebase.
Student flow (replace local debug keystore)
Each student who wants Google Sign-In on the shared Firebase project can install the class debug keystore locally.
- Close Android Studio (recommended).
- Back up the student’s current debug keystore.
- Copy the teacher-provided keystore into
%USERPROFILE%\\.android\\debug.keystore. - Rebuild and run the app.
PowerShell example (student machine):
$targetDir = "$env:USERPROFILE\.android"
New-Item -ItemType Directory -Force $targetDir | Out-Null
if (Test-Path "$targetDir\debug.keystore") {
Copy-Item "$targetDir\debug.keystore" "$targetDir\debug.keystore.backup" -Force
}
Copy-Item "E:\Temp\FromTeacher\debug.keystore" "$targetDir\debug.keystore" -Force
Verification (student machine):
"C:\Program Files\Android\Android Studio\jbr\bin\keytool.exe" -list -v -keystore "$env:USERPROFILE\.android\debug.keystore" -alias androiddebugkey -storepass android -keypass android
The student’s printed SHA1 should match the fingerprint registered in the Firebase project.
Deep Freeze / lab machine note (important)
If classroom machines use Deep Freeze (or similar restore-on-reboot software), this setup may be lost after restart.
Why:
- The default debug keystore path is under the user profile:
%USERPROFILE%\\.android\\debug.keystore - If that profile location is on a frozen drive (usually
C:), Deep Freeze can revert it at reboot
What survives vs what resets:
- Firebase Console SHA entries: survive (cloud-side)
- Local copied
debug.keystore: may be reverted/lost (machine-side)
Practical classroom options:
- Thaw / unfreeze machines before installing the shared debug keystore (best if policy allows)
- Keep the shared keystore on an unfrozen drive or network share and re-copy it at the start of each lesson
- Use a project-specific debug signing config that points to an unfrozen path (advanced setup; can be taught later)
Emulator checklist (Google Sign-In only)
- Use an emulator image with Google Play support
- Google Play Services is available and updated
- Correct SHA1 added in Firebase for the debug keystore in use
google-services.jsondownloaded after app registration / SHA updates when needed- Google provider enabled in Firebase Authentication
Out of scope for this page (can stay in later code lesson if needed)
- Full production-ready account linking flows (Email/Password <-> Google)
- One Tap / Credential Manager migration
- Security rules design